- India
- International
Petya ransomware cyber attack: Not WannaCry, same lock and demand tactic
Petya ransomware has been around since 2016, and so far researchers don’t think it is the same as WannaCry. The attack is believed to have started against an update used on third-party Ukrainian software called MeDoc, used by many government organisations in the country.
 An affected ATM of state-run OshchadBank in Kiev, Ukraine, Tuesday. (Source: AP photo)
An affected ATM of state-run OshchadBank in Kiev, Ukraine, Tuesday. (Source: AP photo)
A new wave of cyber attacks has hit computers and enterprise servers. After the massive WannaCry attack, which impacted over 300,000 computers globally, the new ransomware is Petya, which has hit chiefly Ukraine and Russia, spread elsewhere in Europe, and hit some big firms in the US, besides shutting down operations in Mumbai’s Jawaharlal Nehru Port Trust.
Is Petya the same as WannaCry?
Petya ransomware has been around since 2016, and so far researchers don’t think it is the same as WannaCry. However, the latest attack and that by WannaCry exploited the same vulnerability in Windows systems, known as EternalBlue. Ransomware essentially locks a user out of his or her computer, and asks for a certain amount to be paid. The ransom is usually demanded in Bitcoins before the user can decrypt the hijacked data. Experts say Petya locks the ‘Master Boot Records’ in Windows, which in the words of Microsoft is “the most important data structure on the disk” — it contains all the information on disk partitions as well as the code that allows the operating system to be loaded/booted onto the PC’s memory.
According to security research firm Kasperksy, the newest ransomware could be a variant of Petya.A, Petya.D, or PetrWrap seen earlier, though not on this scale. The firm doesn’t think this is a variation of WannaCry.
So, what is the latest attack doing?
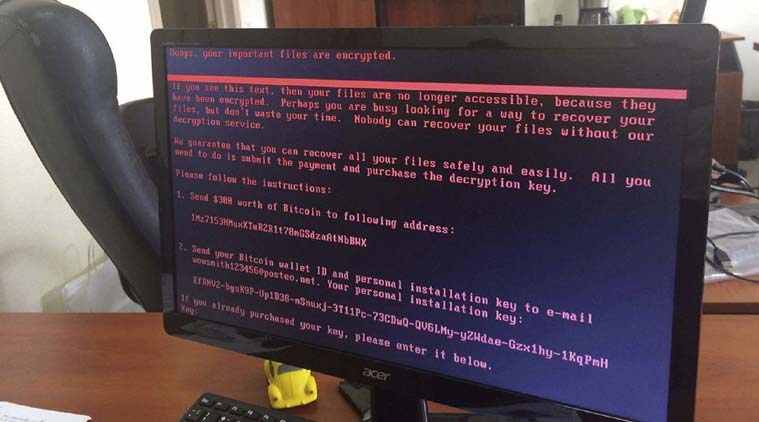
Petya is more advanced ransomware, and researchers are convinced it has no kill switch. Like WannaCry, it locks up a computer’s files and demands $300 in Bitcoins as ransom. All data on a computer gets encrypted, and researchers say there is no way to decrypt it. Once it infects the computer, it will wait for an hour or so, and then reboot the system. After that, the files are encrypted and the user sees a ransom note. Users are also warned against switching off during rebooting. “If you see this text, then your files are no longer accessible, because they are encrypted. Perhaps you are busy looking for a way to recover your files, but don’t waste your time. Nobody can recover your files without our decryption service.”
 The attack is believed to have started against an update used on third-party Ukrainian software called MeDoc, used by many government organisations in the country. (Source: AP photo)
The attack is believed to have started against an update used on third-party Ukrainian software called MeDoc, used by many government organisations in the country. (Source: AP photo)
According to Kaspersky, the hackers have used a “standard, solid encryption scheme” and unless they made a mistake, there’s no way of getting the files back. The security firm calls this a fairly “complex attack” that spreads on to networks quickly. Victims are asked to send the ransom to an address, and then their Bitcoin wallet id via e-mail to wowsmith123456@posteo.net. This is to confirm the transaction has been made.

What is the EternalBlue exploit, and does Microsoft have a fix ?
EternalBlue is a vulnerability that exists in Windows 10, 8, 7, and even XP. EternalBlue was developed by the US National Security Agency (NSA) along with other hacking tools. But this, along with a bunch of others from the company, was leaked online. Microsoft issued a patch in March 2017. However, people don’t always upgrade their PCs or install security updates. The problem is made worse in enterprises where PCs running on Windows might not have been upgraded even after the WannaCry attacks.
How did the ransomware attack start?
The attack is believed to have started against an update used on third-party Ukrainian software called MeDoc, used by many government organisations in the country. Ukraine was the worst affected: Kaspersky’s initial findings say over 60 per cent of attacks took place in Ukraine, and 30 per cent in Russia. In Ukraine, the impact has been wide: from government offices to telecom companies, supermarkets, banks, and even the Chernobyl power plant.
For decrypting files, currently there is no solution. Researchers at Kaspersky say “the ransomware uses a standard, solid encryption scheme”. The firm notes that unless the hackers made a mistake, the data can’t be accessed. Multinational companies such as law firm DLA Piper, shipping giant AP Moller-Maersk, drugmaker Merck as well as Mondelez International, which owns Oreo, Cadbury, were impacted. In the US, some hospitals have been affected. Poland, Italy and Germany are other countries where Petya has made an impact. In India, the Port Trust was hit since AP Moller-Maersk operates the Gateway Terminals India at JNPT. This has a capacity for over 1.8 million standard container units.
So what happens now?
As a first step, the email address being used by the hackers has been suspended by the service provider. In a blog post, Posteo wrote, “We became aware that ransomware blackmailers are currently using a Posteo address as a means of contact. Our anti-abuse team checked this immediately — and blocked the account straight away.” Posteo said it was no longer possible for the attackers to access the email. For users who have lost their data, it means there’s no way of getting the decryption key from the hackers, since the email account has been shut down.
However, according to a tweet from HackerFantastic, when the system goes in for a reboot on its own, the user should power off the computer rather than switch it on. This is because during the reboot the files are being encrypted, and if the computer is switched off during this period, the files remain safe, though still inaccessible. Researchers warn against paying the hackers, saying there is no certainty that they will get the data back.
More Tech
Apr 18: Latest News
- 01
- 02
- 03
- 04
- 05