- India
- International
Govt denies data breach of 7 million BHIM users, cybersecurity firm maintains its claim
Rotem and Locar of vpnMentor said that developers of the CSC-Bhim website could have easily avoided exposing user data if they had taken some basic security measures to protect the data.
 Cybersecurity firm claims BHIM data breach, NPCI denies. (Express Photo: Mohammad Faisal)
Cybersecurity firm claims BHIM data breach, NPCI denies. (Express Photo: Mohammad Faisal)
The National Payments Corporation of India (NPCI) has issued a statement saying there has been no compromise of data on the BHIM app, after Israeli cybersecurity firm vpnMentor’s claims that it had discovered a breach of personal records of around 7 million Indians used to onboard them to the mobile payment app. As per the report, the data was stored on a misconfigured Amazon Web Services S3 bucket and was publicly accessible.
The breach was discovered by Noam Rotem and Ran Locar of the vpnMentor research team who say the exposed records are highly sensitive as it includes many documents needed to open an account on BHIM. The firm said CSC e-Governance Service Ltd (the company which developed BHIM in partnership with the Indian government) established the website connected to the misconfigured S3 Bucket “to promote BHIM usage across India and sign up new merchant businesses, such as mechanics, farmers, service providers, and store owners onto the app”.
According to Rotem and Locar, the breach was first discovered on April 23, 2020, and seem to have contained records from February 2019. It was available publicly until May 22, 2020.
Also read | Is it safe to use Mitron app? Cyber expert says ‘it’s risky”
“We have come across some news reports which suggest data breach at BHIM App. We would like to clarify that there has been no data compromise at BHIM App and request everyone to not fall prey to such speculations. NPCI follows high level of security and an integrated approach to protect its infrastructure and continue to provide a robust payments ecosystem,” the NPCI statement said.

Noam Rotem and Ran Locar told indianexpress.com that it stands by its report and the fact remains that personal data of millions of Indian citizens was left exposed to anyone with a web browser. As per the firm, these records include scans of Aadhaar cards and caste certificates, photos used as proof of residence, professional certificates and degrees, screenshots taken within financial and banking apps as proof of fund transfers, as well as scans of PAN cards.
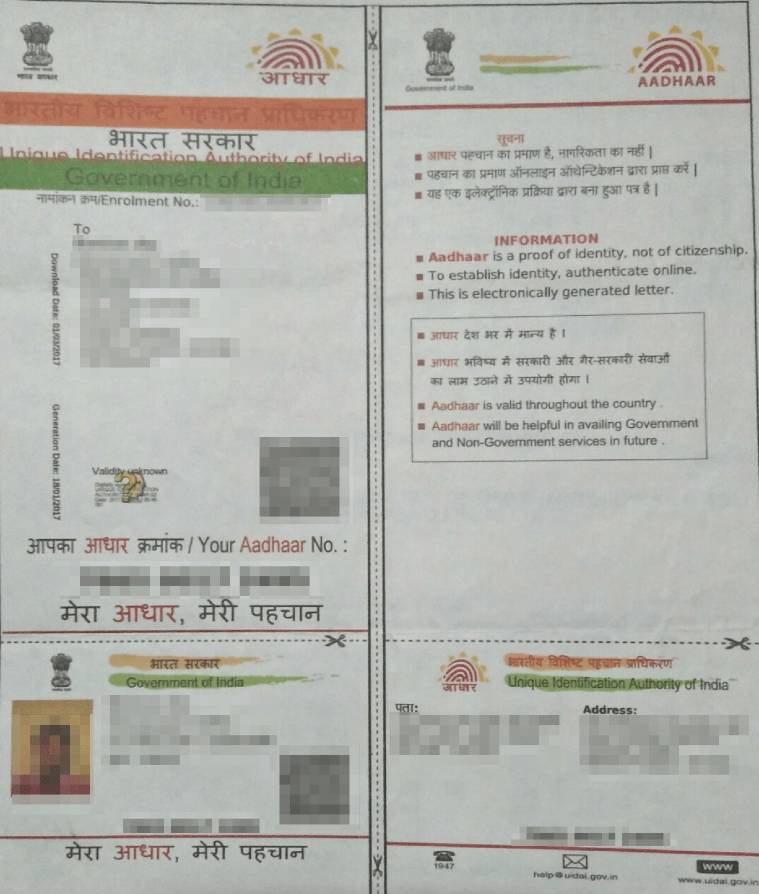 Screenshot of documents shared by vpnMentor in its report.
Screenshot of documents shared by vpnMentor in its report.
The documents not only give a complete profile of individual’s private information such as name, date of birth, gender, address, religion, caste, biometric details, etc. but also their financial and banking records, thus exposing them to potential fraud, theft, and attack from cybercriminals.
 Screenshot of documents shared by vpnMentor in its report.
Screenshot of documents shared by vpnMentor in its report.
“The attempts by various parties in India to deny our findings are sad. The fact remains that PII [personal identifiable information] data of millions of Indian citizens was left unprotected on a public bucket named after CSC BHIM, and instead of looking into the faults that lead to this breach and make sure they won’t happen again, we are faced with ridiculous claims it never happened,” Rotem and Locar said.
 Screenshot of documents shared by vpnMentor in its report.
Screenshot of documents shared by vpnMentor in its report.
“We managed to confirmed CSC BHIM as the owner of the bucket in our research. The CSC-Bhim site (cscbhim.in) mentions NPCI and Punjab National Bank as their partners. The site features photos from BHIM drives in various parts of India, under the BHIM logo. The site itself bears the BHIM logo, as well as that of the Indian Ministry of Electronics and Information,” they said.
Rotem and Locar said having such sensitive financial data in the public domain or the hands of criminal hackers would make it easy to trick, defraud, and steal from the people exposed. “BHIM app users could be exposed to identity theft, tax fraud, theft (hackers accessing the BHIM accounts via the app and withdraw money), or even fraud (tricking a user into sending you money via the app— by sending texts or emails imitating businesses and friends,” they said.
Also read | Covid-19 test kits, PPE, antiviral drugs on sale at Dark web’s pandemic sale
In their report, vpnMentor claimed the data was stored on a misconfigured AWS S3 bucket. The Amazon Web Services’ (AWS) Simple Storage Service (S3) is a public cloud storage resource. “AWS is absolutely not involved in this. BHIM used their service and didn’t implement the correct access rules,” they said.
Rotem and Locar also said the developers of the CSC-Bhim website could have easily avoided exposing user data if they had taken some basic security measures to protect the data. “It would have required from them to configure their bucket in a way that only the people authorised could access the bucket and the files.”
In its data breach report, vpnMentor had mentioned that S3 bucket carried screenshots of documents like Aadhar card, caste certificate, residence proof and more that were stored in the misconfigured S3 bucket. However, the CSC e-Governance Service told the Times of India that the project did not involve taking Aadhaar data of any merchant, therefore there is no question of any identifiable personal information to be made public.
Rotem and Locar asserted the CSC claim goes against the evidence they have. “We are confused about this claim, as it is not supported by the evidence we have shared with the Indian authorities… As you can see in our report (screenshots), we did find Aadhar cards as well as other personally identifiable information,” they said.
More Tech
Apr 24: Latest News
- 01
- 02
- 03
- 04
- 05







































