
Researchers have linked the APT15 hacking group known for Android spyware apps to a Chinese military company, Xi'an Tian He Defense Technology Co. Ltd.
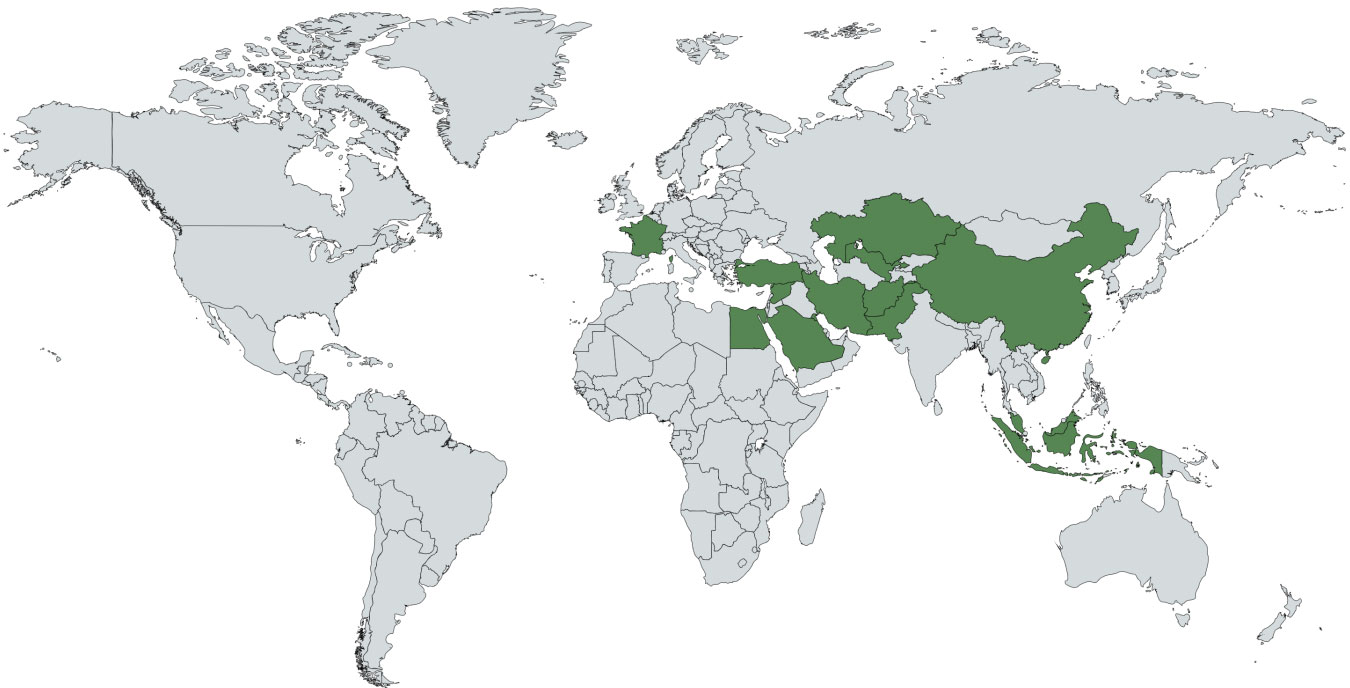
In a new report by Lookout Threat Intelligence, researchers show how four Android "surveillanceware" tools used to target the Uyghur ethnic minority group are part of a more extensive mobile advanced persistent campaign that has been operating for years.
While the origins of the activity can be traced back to as far as 2013, Lookout has been monitoring malware families since 2015 named SilkBean, DoubleAgent, CarbonSteal, and GoldenEagle that were distributed as Android apps.
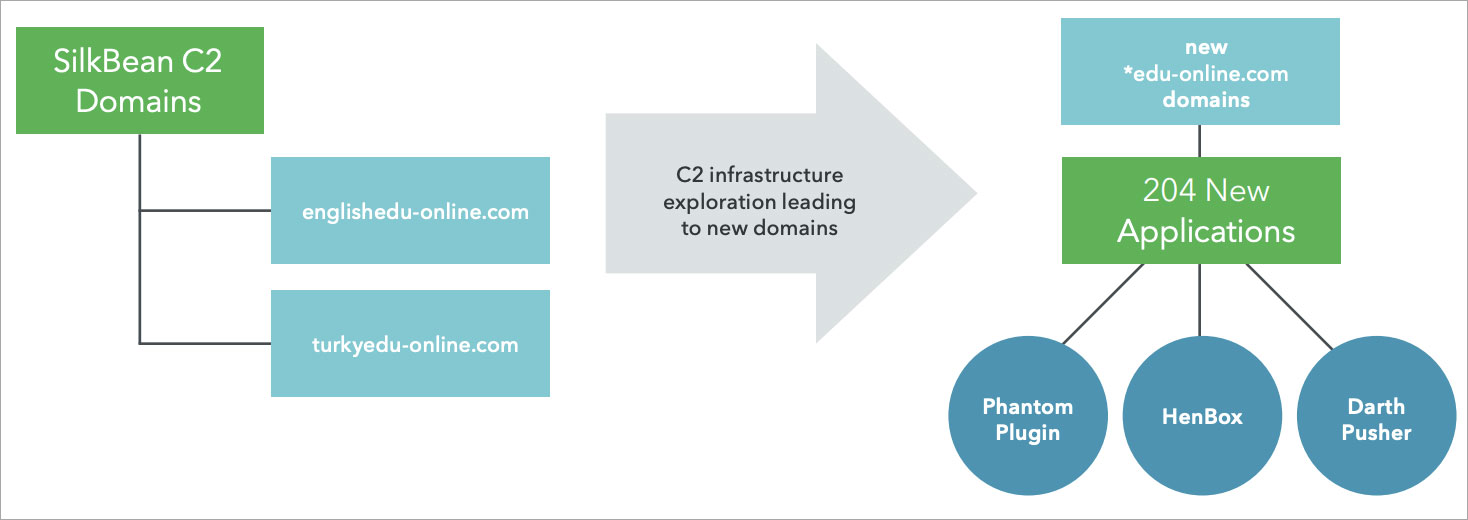
The campaign also relied on other known tools to aid in its surveillance operations called HenBox, PluginPhantom, Spywaller, and DarthPusher.
The motivation behind the large scale surveillance operation on ethnic minorities, both within and outside of China, has been attributed to the Chinese government’s national security and counter-terrorism efforts.
Moreover, the period in 2015 which is when the mAPT malware development peaked, follows shortly after the “Strike Hard Campaign against Violent Terrorism (严厉打击暴力恐怖活动专项行动)” campaign having been put in place in May 2014, making this coincidence noteworthy.
Source: Lookout
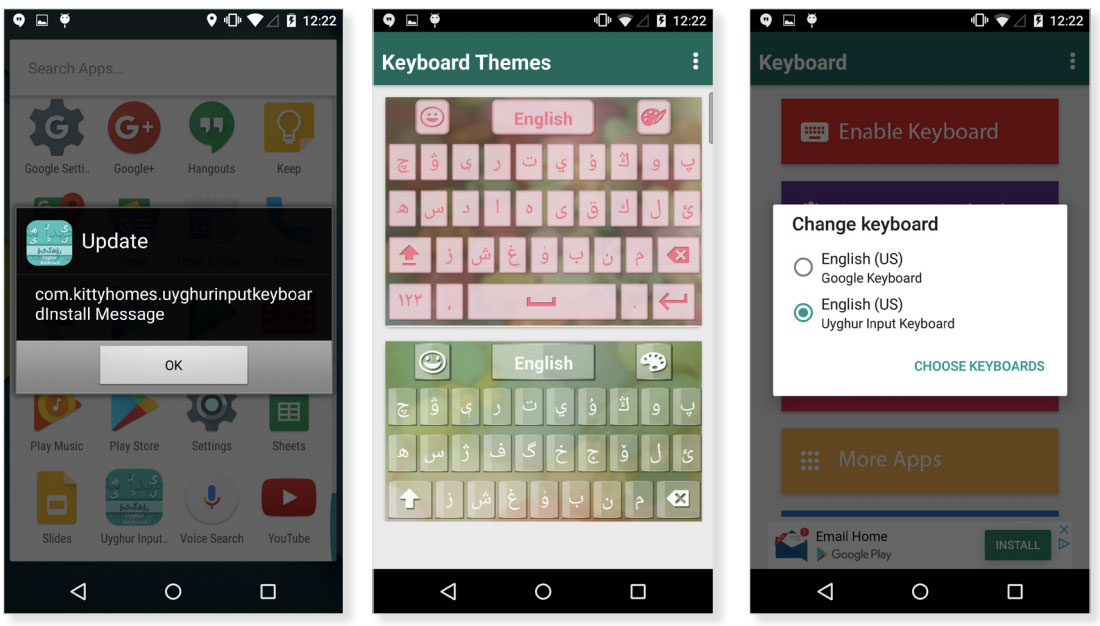
Malware distributed in the form of Android apps
To distribute their surveillance malware, APT15 incorporates it into Android apps that are then targeted at various groups.
As an example, the “Uyghur Keyboard app” targets the Uyghur ethnic minority group with the SilkBean malware, as shown below.
Source: Lookout
The four malware families have advanced surveillance capabilities, including remote code execution, accessing call history and messages, taking screenshots and photos from the device, proxying the Internet traffic, recording audio from surroundings and phone calls, and requesting administrator permissions.
The associations between the surveillance tools, as well as the four families of Android surveillanceware (SilkBean, DoubleAgent, CarbonSteal, and GoldenEagle) are mainly due to the tools using shared infrastructure and C2 domains, similarities between code-signing certificates, and code overlap.
Additionally, analyzing WHOIS data for C2 domains also helped map the different malware strains to the responsible entities.
The group, APT15, behind these activities is also known by other monikers: GREF, Ke3chang, Mirage, Vixen Panda and Playful Dragon.

Source: Lookout
To make the malicious Android apps difficult to distinguish from legitimate apps, some SilkBean samples share names with innocuous-sounding Android services such as com.google.pay and com.android.google.service.
However, instead of using the Google Play store to distribute malicious apps, the hackers relied on (possibly compromised) third-party sites and forums visited by their target victims that redirected to servers where these malicious apps were hosted.
“Two C2 server domains retrieved from the settings files from SilkBean samples are www.englishedu-online[.]com and www.turkyedu-online[.]com. Navigating to these sites early on in the investigation redirected the request to a third-party app store called www.islamapk[.]com which hosts Uyghur and Islamic specific applications for download,” the report stated.
Source: Lookout
How the defense company was exposed
While investigating the IP addresses and malicious domains used by these malware samples, Lookout researchers came across an Admin Panel used by the C2 servers.
This panel was unsecured and allowed the researchers to see the IP addresses and GPS coordinates of the target Android phones, among other vital pieces of information.
“Among the content accessible was a management panel that contained email addresses of targets, what we believe to be GPS coordinates of target devices, IPs of admin logins and target devices, and evidence that phishing campaigns were being run from the same infrastructure.”

Source: Lookout
However, given the timestamps on these records and their early malicious activity logged by the panel, the target devices were most likely mock devices used by the creators of the malware for testing purposes.
Through the GPS coordinate data associated with these devices, Lookout researchers were able to conclude the malicious activity had roots in the Chinese military company, Xi'an Tian He Defense Technology.

Source: Lookout
A complete list of C2 domains mapped to a specific malware family is provided on page 15 of the report, along with Indicators of Compromise (IOCs) such as SHA1 hashes that can be used to spot malicious activity.
Reports of Chinese malware groups conducting espionage, like those behind Dudell and PKPLUG are not novel.
This scale's massive operation opens up many questions about government surveillance, citizen privacy, and user device security.
Researchers may have successfully uncovered this particular operation and the entities behind them. However, there remain unknown unknowns in this dark side of technology and what may be about to come.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now