Six ways GRC tech can help organizations meet CMMC requirements

All organizations have to monitor and protect data. But, monitoring and protecting data is even more essential for those that work with the Department of Defense (DoD). The DoD has witnessed a growing number of threats, vulnerabilities, and cyberattacks aimed at its contractors. As a result, the DoD has established a framework for companies to adhere to, to prove compliance in protecting defense data.
The framework is called Cybersecurity Maturity Model Certification (CMMC). And, like CCPA or HITRUST, specifies a unified set of cybersecurity standards required by all DoD contractors by the end of 2020. While old DoD compliance standards allowed self-certification, CMMC requires third-party validation to compete for government contracts. Certified organizations must be audited every three years to verify ongoing compliance.
Types of Data
Before diving into the CMMC Framework, it’s worth diving into the types of data and their definitions. Anyone contracted with the DoD has access to at least one type of information: Controlled Unclassified Information (CUI) or Federal Contract Information (FCI).
CUI is a long laundry list of protected information in categories like immigration, nuclear, critical infrastructure, defense, international agreements to NATO, and tax information.
FCI is provided by or generated for the government under a contract to develop or deliver a product or service to the government.
CMMC Framework
The CMMC has five levels of compliance, ranging from basic to advanced. Contractors must prove capabilities of each level in order to advance and bid on contracts that require higher levels of security because of increasingly sensitive data.
- Level 1: Basic safeguarding of FCI
- Level 2: Transition step to protect CUI
- Level 3: Protecting CUI
- Levels 4-5: Protecting CUI and reducing risk of Advanced Persistent Threats
CMMC For Your Organization
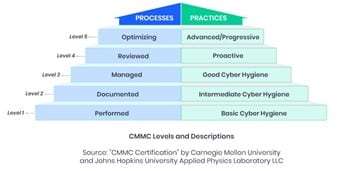
As you can see, the different levels of CMMC compliance enable organizations to meet a level of compliance that works for them. If the organization isn’t prepared to meet level five requirements, it can still land at level two and work up to level five.
In order to evaluate the level at which your organization’s cybersecurity program currently stands, you’ll need to conduct an audit. Governance, risk, and compliance (GRC) platforms are extremely effective in these situations as they create an audit log of standards met, making it very easy to show compliance. It can also centralize data, create workflows, and serve as a tool to map controls which is all very handy in facilitating the CMMC process.
Here are six expanded ways GRC platforms can help prepare an organization for CMMC compliance.
- Reporting: Information is stored in such a way that anyone needing third-party verification or an audit trail can access it
- Access Control: Helps manage different levels of access to CUI with varying levels of approvals across individuals or departments
- Threat Assessments: Where an organization can evaluate strengths, vulnerabilities, and even gaps in current cybersecurity processes in order to patch them for CMMC certification
- Incident Reporting and Mitigation: Points the right reporting, incident management, and mitigation tools to the right people at the right time to safeguard DoD assets
- Cross-divisional Collaboration: Enables compliance through collaboration, coordination, and information sharing through divisions
- Process Management: Establishes a platform/tool of record for information security risk to manage processes and practices for specified domains
Working on behalf of the DoD is not to be taken lightly. By understanding the compliance standards set in place by the CMMC and evaluating current practices, you can set your organization up for success. And, for organizations that don’t currently work with the DoD, CMMC compliance is worth looking into in order to create new revenue streams. A GRC platform is one tool to assist in the process, helping your team determine readiness, uncover vulnerabilities, patch any areas of weakness, and set up the proper processes to meet and retain compliance.

Jon Siegler is the Co-Founder and Chief Product Officer at LogicGate. He has over a decade of experience in designing customer-centric enterprise risk and compliance systems, delivering value for organizations by reducing their risk, improving efficiency, and automating processes. Jon is driven by a passion to connect deeply with our customers' problems in order to build an amazing product that makes the challenges of risk and compliance easier.